Computers and Mobile Phones
This page focuses on security and privacy for Computers and Mobile Phone, including applications, email and user accounts
Security and Privacy Guidance for Sensitive Devices
Applications Advice: Be very picky about what you install. Stick to the recognized application stores (Apple’s App Store for iOS and macOS, Google’s Play Store and/or Amazon’s Appstore for Android, Microsoft Store for Windows), but also check reviews and ratings before downloading - a recognized store does not guarantee an application is safe. For specific software (like Adobe, Microsoft Office, etc.), downloading directly from the developer’s website is likely the safest option - always check the url carefully. Update the Apps that you use as these often include security updates. Disable and Remove Apps that you no longer use.
Device hardware should receive security updates to close new vulnerabilities as they are discovered - if they are no longer supported by the manufacturer, it may be time to replace them. For example, Android phones support (security updates) may be as little as 3 years or as many as 7 years.
Using a Password Manager helps you use Passkeys (preferred) or Unique Passwords on your accounts. Creating your own passwords is not recommended due to both credential stuffing and brute force attacks. Passkeys (which are tied to specific device) are more secure than passwords.
Consider an Authenticator Application: Authenticator hardware (FOB) or authenticator apps are stronger than a texted code to your phone since your phone could be compromised via a SIM card Swap.
Use Privacy and Security Settings (on devices/operating systems and within browsers or applications; review them for use periodically - for example, OS functions such as Apple’s Private Relay.), Limit Sharing on Social Media (the less the better). Browsers should leverage security and privacy settings available including items such as hiding IP address, and preventing cross-site tracking. Location Services should be set to Never unless functionally necessary or desired (for example, a Map application or Camera which can be set to active only when using the application). Always restrict application permissions to the greatest reasonable extent.
Anti-virus and VPN: Bucks County Home Networks acknowledges the value of additional anti-virus software and VPNs - more protection is better protection, but also aims for enough protection based on individual behaviors. Noting that operating systems (Windows, macOS, iOS, Android) all include anti-virus and privacy functions, not having an explicit 3rd party anti-virus or VPN service does not leave an individual unprotected; however, insure that the OS is properly configured for your needs (for example, enabling Private Relay in macOS and iOS although the configuration requires using Safari). If you want the extra protection afforded by 3rd party software, do your homework. Realize too that some VPN services include an anti-virus function that examines downloads before it ever gets to your device (an example is NordVPN).
Phishing (pronounced “fishing”) and Scams: come in many forms and may look like something from someone you know - email and text messages with links or attachments, phone calls, messages indicating you won a prize or an undeliverable package or order confirmation, messages asking for any kind of personal information, fake websites, fake ads, surveys, on-line quizzes, and even links within legitimate websites that have been compromised. Just because something looks like it came from a friend or family member does not mean that it actually did - and even if it did come from someone you know or trust does not mean that it is safe.
Do NOT click the link and Do NOT provide requested information unless you are certain that you initiated the contact directly with the organization requesting the information. SLOW DOWN and TRUST SLOWLY when navigating online.
More information on phishing is available from the National Institute of Standards Technology (NIST), a group within the US Department of Commerce (again, right click to copy the link, paste it into your browser address bar and verify):
https://csrc.nist.gov/projects/human-centered-cybersecurity/research-areas/phishing
Caution Summary: Assume your private information is already available to bad actors, but protect your information anyway. Strong passwords and strong authentication are important safeguards. Be aware of third-party apps, impersonation attempts, and ensure software is up to date. Be skeptical of unsolicited messages and links, especially from unknown accounts. Be aware of common warning signs that your information is actively being exploited such as Account access problems, Notifications of unexpected transactions or activity - may indicate a stolen credit card, or Problems sending texts - may indicate stolen phone number (also called a SIM card Swap).
Zero Trust, Least Privilege and Defense in Depth should be reflected in both your mindset and your device configurations.
Computers and Mobile Phones
Use Multi-factor Authentication
Use current Encryption algorithms (typically WPA3).
Safeguard Against Eavesdropping by restricting microphone or camera use, and limit location sharing.
Schedule Device Reboots to help remove potential malware.
Turn off bluetooth if it is not needed (especially on mobile device).
Disable WiFi on any device that doesn’t need it (including cell phone when traveling). Avoid public WiFi, including hotels, public venues (stadiums) and coffee shops - do not connect automatically; Cellular is more secure than public WiFi.
Exercise Secure User Habits - back up data, use secure storage methods, and enable account recovery options. Enable Full Disk Encryption to make disks unreadable to an attacker and Create Restore Points in case of compromise.
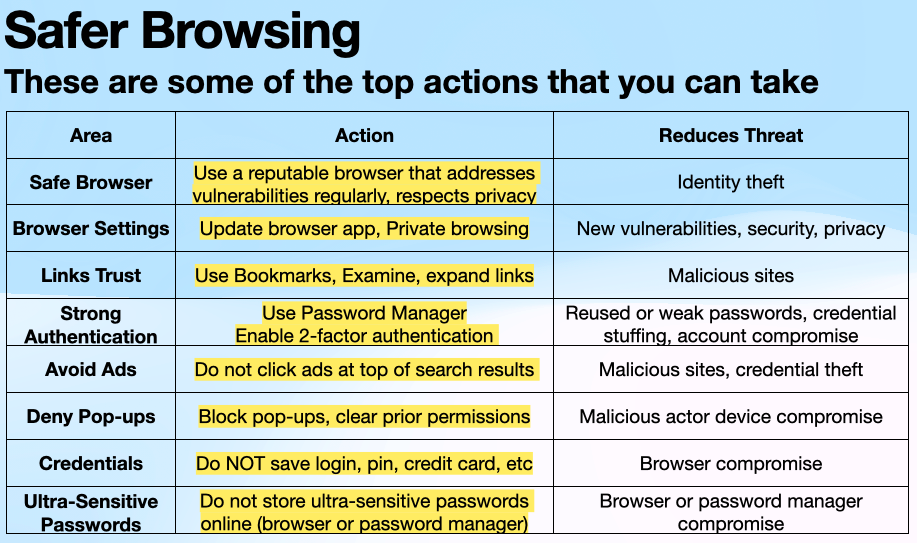
Browsing the Web and Web Based Applications Advice:
Do NOT click any link or open any file that you are not sure about.
Use a Modern Browser and keep it updated for better security.
When browsing on the internet, verify the address bar has a “lock” or begins with https:// indicating a secure connection as well as the actual address you want to reach. Using Bookmarks for often used accounts is recommended, but still verify the domain (part of the url right before the .com or .org).
Consider switching to a browser such as Brave, which is “privacy by default,” blocking ads and trackers, and also changing the search engine to DuckDuckGo, which is also “privacy by default” with a better user experience. Use a Password Manager and opt for Passkeys if the application supports them. Use Encryption. Attackers may mimic a real site in the hope that an unwary user will download malware - this specifically includes the Ads that typically come through at the top of a search result (avoid all Ads at the top of a search). Use the privacy settings in a browser to limit tracking.
Computers and Mobile Devices Advice:
Shut down computer when not in use.
Upgrade Operating Systems Automatically for the latest security updates
Employ Security Software - enable firewall, use antivirus and anti-malware software (computer and mobile phone OS typically include antivirus and anti-malware software - there are also fee-based 3rd party software that can be used)
Protect Passwords by using a password manager to keep passkeys and/or passwords complex and unique.
Personal Accounts (Email and Phone)
Email Advice: Do not open ANY unsolicited or unexpected attachments or links - this includes that link that your friend sent you. Do not share personal or financial information via email as companies do not (and should never) ask for it through e-mail; always contact the company directly via known contact paths such as a bookmark of a verified secured url. Consider having one primary email address for sensitive accounts and do not use this on other accounts (such as social media). Verify your email client uses TLS (Secure IMAP or Secure POP3). Protect email access with a strong password with 2FA noting that a passkey or an authenticator app is better than text verification (SMS). Check sender email addresses being cautious about spoofed addresses and suspicious senders.
Text Messaging Advice: Do not open or click ANY link in text messaging. Do not send sensitive information via text without an end to end encryption application such as Signal.
Phone Advice: Lock down your account changes with your carrier (methods may vary by carrier). Do NOT answer calls from unrecognized numbers (a legitimate caller will leave a message - be skeptical and trust slowly).
NOTES: Financial institutions, health insurance and other account verifications may use email or text messaging to verify a user login. Email accounts may be taken over and Text messages can be intercepted (it is much better than nothing, but a 2FA application or token is better). SMS, MMS and RCS Text messaging does not have end to end encryption support (your cellular carrier can see your messages and protocol weaknesses may allow others to see them too). Messaging on Android and iOS can be encrypted end to end with special purpose applications such as Signal and WhatsApp (a Meta owned application). Comparing the two applications on privacy and security, Signal application is recommended for its superior transparency and privacy policies. Both sender and receiver have to have the same application to communicate.
Phone Number: Be aware that a scammer may target your cellular carrier to steal your phone number (SIM swap) after which the scammer may attempt to impersonate you and would be able to use 2 factor authentication (by receiving the texted code on your phone number) to potentially login to you financial accounts.